Fortifying Security: Our IASME Cyber Essentials Journey
In today’s digital landscape, safeguarding sensitive data and ensuring robust cybersecurity measures are paramount for any business. As technology advances, so do the threats posed by cybercriminals. Understanding the importance of fortifying our defences against these threats, we embarked on a journey to attain the prestigious Cyber Essentials Certificate from the IASME Consortium.
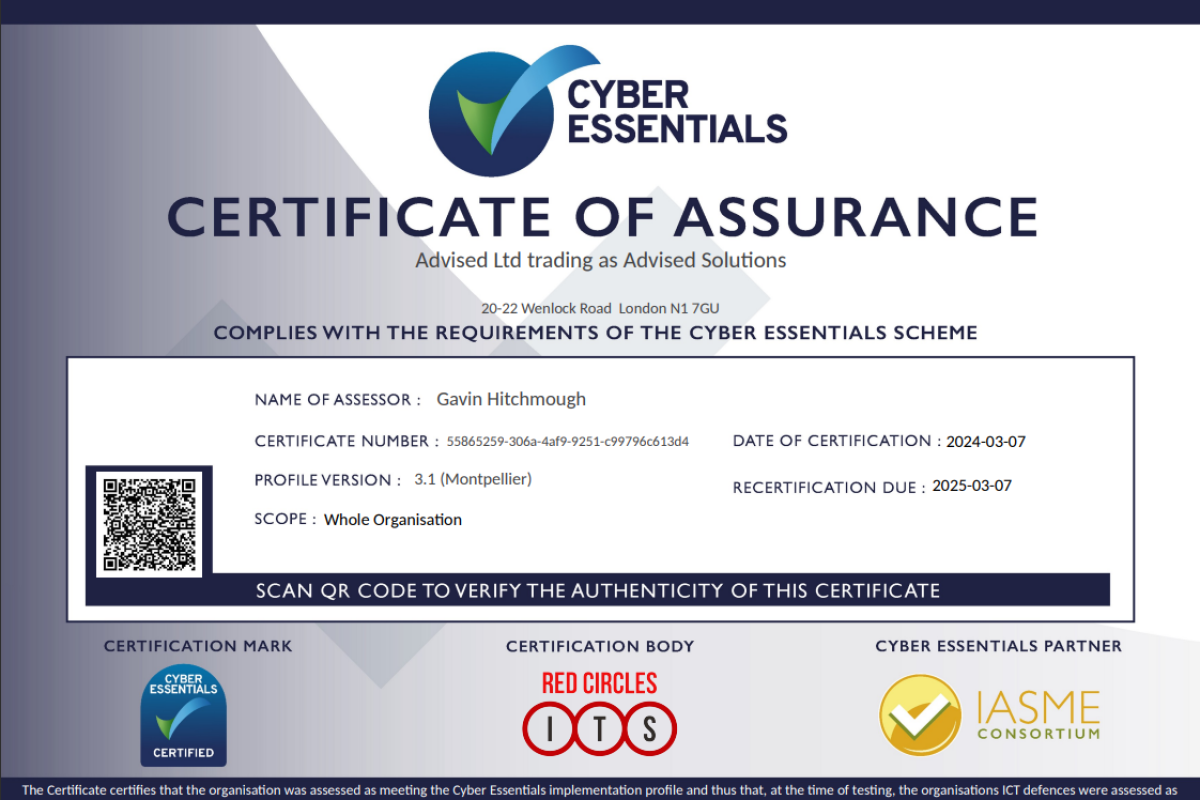
We’re thrilled to announce our attainment of the IASME Consortium’s Certificate of Assurance for Cyber Essentials, a testament to our unwavering dedication to safeguarding sensitive data and fortifying our defences against evolving cyber threats.
The IASME Consortium’s rigorous assessment process scrutinizes various facets of an organisation’s security infrastructure, from governance and risk management to technical controls and resilience. By completing this assessment, we’ve not only validated our current security measures but also showcased our commitment to industry best practices.
This certification enhances trust among our stakeholders by assuring them that their data is protected within our digital ecosystem. It also provides potential clients and partners with the assurance that we prioritise cybersecurity and are equipped to mitigate risks effectively.
However, achieving the IASME Certificate of Assurance for Cyber Essentials isn’t just a milestone; it’s a continuous journey. We’re committed to remaining proactive and adaptive in the face of evolving threats, investing in the latest tools, technologies, and training to maintain robust defences.
As we celebrate this milestone, we reaffirm our commitment to excellence and pledge to remain at the forefront of cybersecurity innovation.
What does Cyber Essentials include?
Below are the five core controls of Cyber Essentials:
01.
Firewalls
Firewalls act as a barrier between a trusted internal network and untrusted external networks, controlling incoming and outgoing network traffic based on predetermined security rules.
02.
Secure Configuration
Ensuring that all systems and devices within the network are configured securely, minimizing vulnerabilities and reducing the potential for unauthorized access or exploitation.
03.
Security Update Management
Regularly updating software, applications, and systems with the latest patches and security updates to address known vulnerabilities and protect against emerging threats.
04.
User Access Controls
Implementing mechanisms to manage and restrict user access to sensitive data and resources based on the principle of least privilege, reducing the risk of unauthorized access or misuse.
05.
Malware Protection
Deploying antivirus software and other malware detection tools to detect, prevent, and remove malicious software, such as viruses, worms, and ransomware, from infecting systems and compromising data.
Protecting your data!
In today’s digital age, where cyber threats lurk around every corner, trust is paramount. That’s why we’ve gone the extra mile to attain the prestigious IASME Certificate of Assurance for Cyber Essentials, validating our dedication to industry-leading security practices.
Trust Advised Solutions with what matters most—your data.